Secure Campus transformation with new LISP Pub-Sub and Multi Zones features.
Recently we assisted customers with POC and Design of their brownfield campus to Cisco’s ZTNA architecture (SD-Access, ISE, and FTD). In this design, we leveraged some of the latest Cisco SD-Access features to satisfy customer’s unique use cases and further secure and simplify their network.
Some of the customer requirements:
- Zero trust network access (ZTNA) with granular segmentation using SGTs
- Flexibility for granular control of IP pool provisioning
- Different IP subnets for each floor for the same user groups
- Minimize the complexity of route learning and redistribution between BGP/LISP
- Address Border convergence issues
- Minimize firewall rule changes for north-south traffic
We used the new SD-Access features; LISP PubSub and Fabric Zones.
LISP PubSub:
The LISP PubSub the Control Plane (CP and TCP) becomes the publisher, and the Border router becomes a subscriber to exchange the LISP information, for example, endpoint identifier (EID) and routing locator (RLOC) information. This eliminates the need for redistribution between BGP and LISP, which results in configuration simplification. For example, VPNv4 IBGP sessions between border routers are not required to avoid border convergence issues. This feature is supported by DNAC 2.2.3.x and switches with 17.7.x software versions.
Fabric Zones:
The fabric zone is the construct in SD-Access. This is an optional construct that provides the flexibility to assign and map selective IP pools within the VNs to be provisioned at the fabric edges. So, for example, in this large brownfield deployment, a customer has different IP subnets for each floor, which results in many VLANs on each fabric edge switch. To simplify it, we configured a primary zone on each floor so that only VLANs used by that floor are created on corresponding access switches.
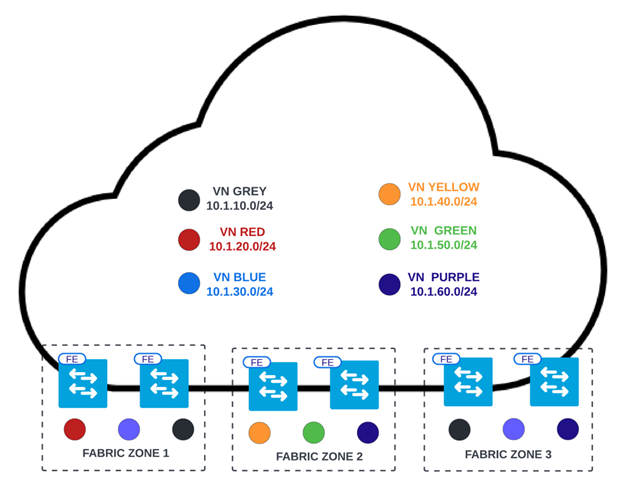
The multi-site and fabric zone allowed users to use single VLAN names across the sites to reduce the number of Cisco ISE policies and significantly simplify their zero-trust network access (ZTNA) architecture.
Conclusion: Leveraging the latest ZTNA architecture features, the customer achieved granular segmentation while simplifying the configuration and convergence complexities.
