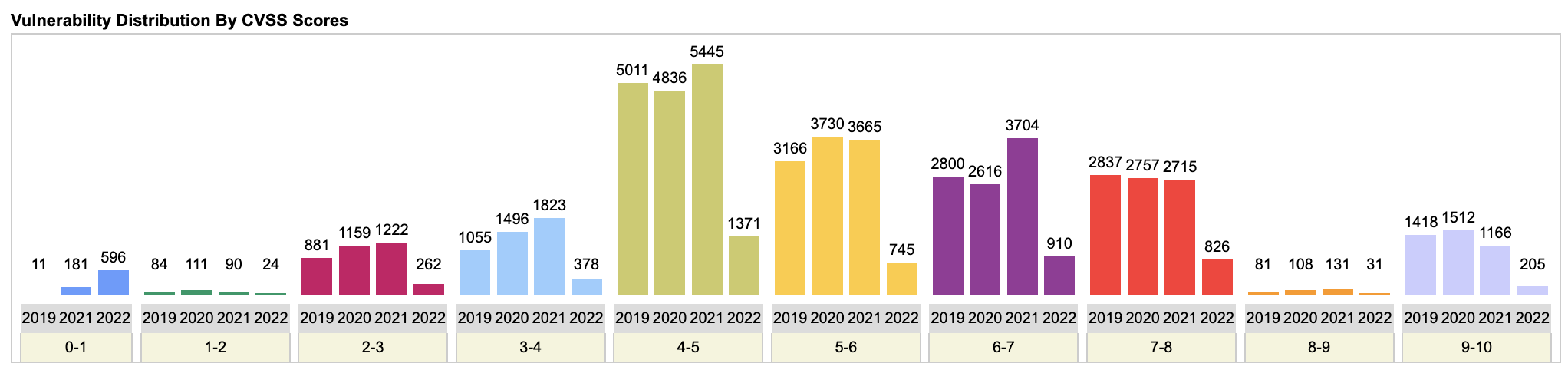
If you think doing a one time or even once a year vulnerability assessment of your digital assets (networks, end points, software, SaaS / Cloud platforms etc..). Think twice. Even during the pandemic period where companies were busy dealing with securing the remote work environment for their employees, and dealing with patching existing vulnerabilities at a fast pace, there was no letting up of new vulnerabilities found in 2020 and 2021. Not only the raw overall vulnerabilities count were more than the pre-pandemic years, medium/high/critical vulnerabilities were almost the same as previous years. If 2022 numbers so far are any indication, we are well on our way to have a record year of reported net new vulnerabilities. It is important for organizations to have a robust, ongoing vulnerability management plan in place and work their MSSPs closely to setup periodic (preferably monthly) vulnerability assessments and ongoing management.
Vulnerability Distribution By CVSS Score (Courtesy cvedetails.com)